Cisco Meshed Wireless LAN Controller Impersonation Vulnerability
 Friday, March 17, 2017 at 10:27AM
Friday, March 17, 2017 at 10:27AM -
A vulnerability in the mesh code of Cisco Wireless LAN Controller (WLC) software could allow an unauthenticated, remote attacker to impersonate a WLC in a meshed topology.
The vulnerability is due to insufficient authentication of the parent access point in a mesh configuration. An attacker could exploit this vulnerability by forcing the target system to disconnect from the correct parent access point and reconnect to a rogue access point owned by the attacker. An exploit could allow the attacker to control the traffic flowing through the impacted access point or take full control of the target system.
Cisco has released software updates that address this vulnerability. Note that additional configuration is needed in addition to upgrading to a fixed release. There are no workarounds that address this vulnerability.
This advisory is available at the following link:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170315-wlc-mesh
-
Vulnerable Products
This vulnerability affects the following products running a vulnerable version of Wireless LAN Controller software and configured for meshed mode:
- Cisco 8500 Series Wireless Controller
- Cisco 5500 Series Wireless Controller
- Cisco 2500 Series Wireless Controller
- Cisco Flex 7500 Series Wireless Controller
- Cisco Virtual Wireless Controller
- Wireless Services Module 2 (WiSM2)
Refer to the "Fixed Software" section of this security advisory for more information about the affected releases.
To determine whether a WLC is configured for meshed mode, use the show ap config general command and verify that the AP mode is set to Bridge. The following example shows a WLC configured for meshed mode:
Cisco AP Identifier.............................. 23 Cisco AP Name.................................... ap1 [...] AP Mode ......................................... Bridge AP Role ......................................... RootAP
[...]
Note: Meshed mode is not enabled by default.Products Confirmed Not Vulnerable
No other Cisco products are currently known to be affected by this vulnerability.
The following products are not affected by this vulnerability:
- Integrated controller in Cisco Catalyst 3850 Series Switch
- Integrated controller in Cisco Catalyst 3650 Series Switch
- Cisco Mobility Express
- Cisco 5760 Wireless LAN Controllers
-
There are no workarounds that address this vulnerability.
-
Cisco has released free software updates that address the vulnerability described in this advisory. Customers may only install and expect support for software versions and feature sets for which they have purchased a license. By installing, downloading, accessing, or otherwise using such software upgrades, customers agree to follow the terms of the Cisco software license:
http://www.cisco.com/en/US/docs/general/warranty/English/EU1KEN_.htmlAdditionally, customers may only download software for which they have a valid license, procured from Cisco directly, or through a Cisco authorized reseller or partner. In most cases this will be a maintenance upgrade to software that was previously purchased. Free security software updates do not entitle customers to a new software license, additional software feature sets, or major revision upgrades.
When considering software upgrades, customers are advised to regularly consult the advisories for Cisco products, which are available from the Cisco Security Advisories and Alerts page, to determine exposure and a complete upgrade solution.
In all cases, customers should ensure that the devices to upgrade contain sufficient memory and confirm that current hardware and software configurations will continue to be supported properly by the new release. If the information is not clear, customers are advised to contact the Cisco Technical Assistance Center (TAC) or their contracted maintenance providers.
Customers Without Service Contracts
Customers who purchase directly from Cisco but do not hold a Cisco service contract and customers who make purchases through third-party vendors but are unsuccessful in obtaining fixed software through their point of sale should obtain upgrades by contacting the Cisco TAC:
http://www.cisco.com/en/US/support/tsd_cisco_worldwide_contacts.htmlCustomers should have the product serial number available and be prepared to provide the URL of this advisory as evidence of entitlement to a free upgrade.
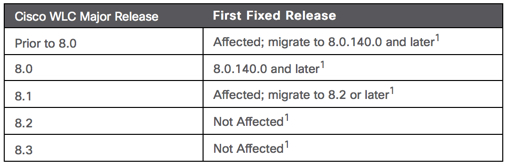
Fixed Releases
Customers should upgrade to an appropriate release as indicated in the following table:















Reader Comments