|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
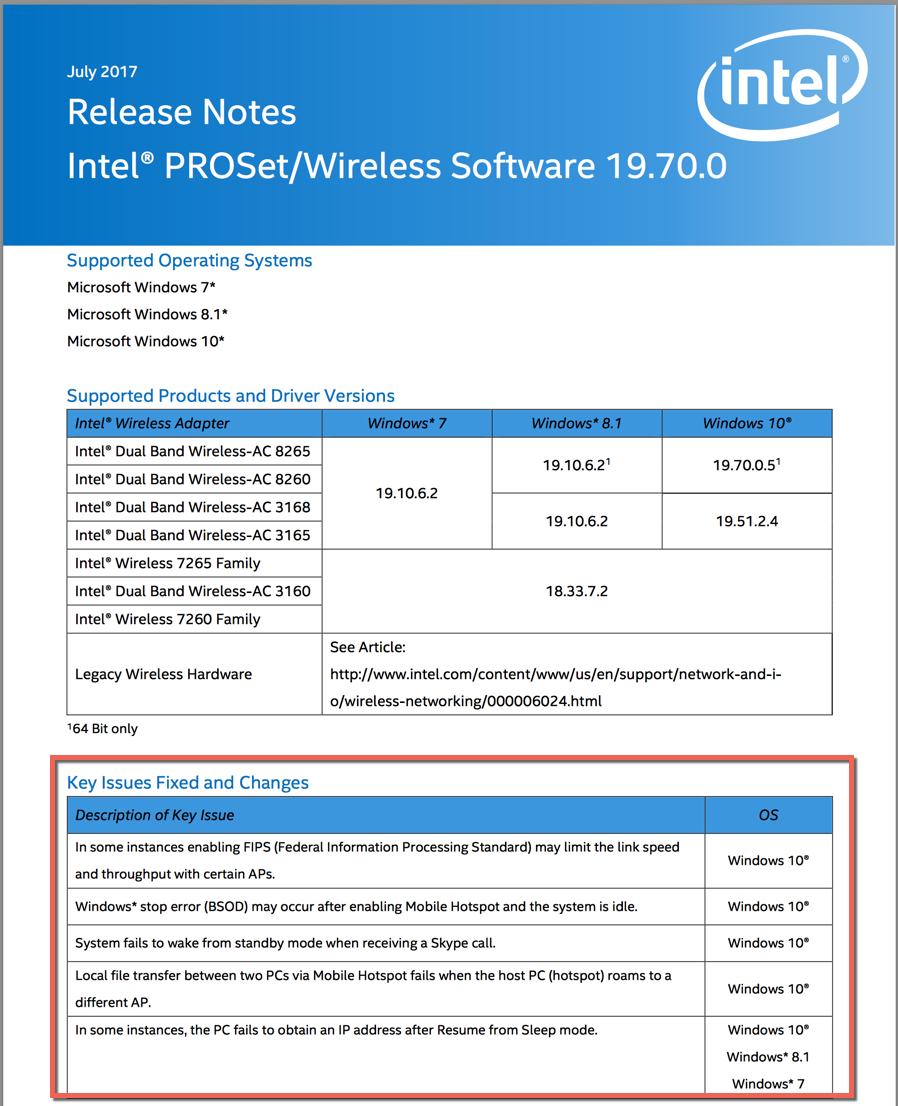
CSCug98522
|
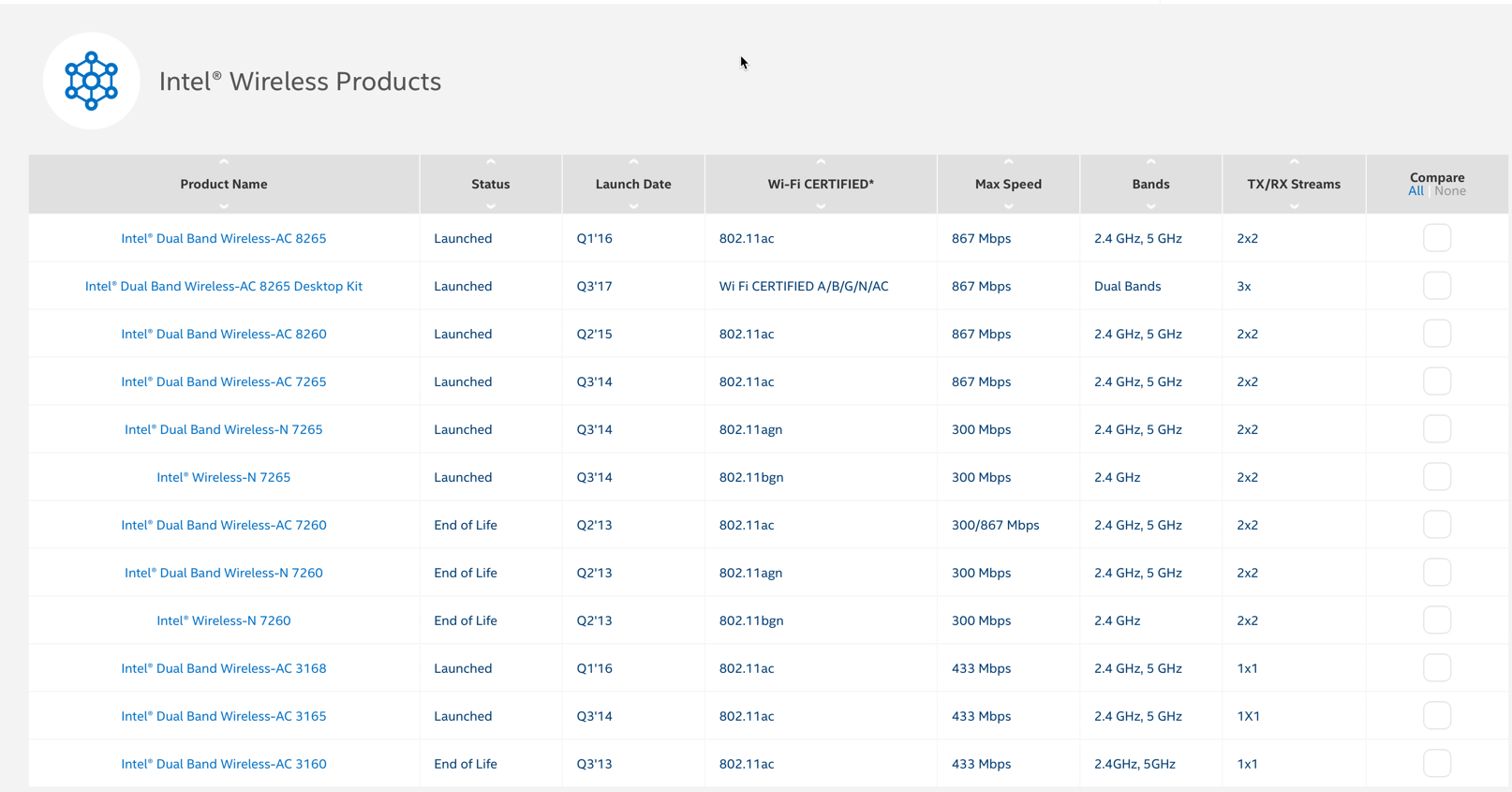
PMIPv6: MAG delivering multiple DNS servers to clients
|
|
|
|
|
|
|
CSCuq05475
|
Controller GUI shows AP's NAT IP instead of private
|
|
|
|
|
|
|
CSCut42406
|
Ct5508 crashed while disabling Mobility oracle.
|
|
|
|
|
|
|
CSCuu91943
|
8510 WLC crash while accessing the controller crash file info thro GUI
|
|
|
|
|
|
|
CSCuw28141
|
Reaper Reset: Task "SNMPTask" missed software watchdog
|
|
|
|
|
|
|
CSCuw30129
|
Debugging logging quickly falls behind real-time
|
|
|
|
|
|
|
CSCuw36069
|
Threshold MIBs incorrectly set for WSSI modules.
|
|
|
|
|
|
|
CSCuw65706
|
AP1530 WGB Drops Tx used w/ other 1530 WGB in same MAC address range
|
|
|
|
|
|
|
CSCuw89229
|
Mesh instability with fast-convergence when RF link is unstable
|
|
|
|
|
|
|
CSCux22620
|
8510 WLC crash in radiusTransportThread system task
|
|
|
|
|
|
|
CSCux28775
|
WLC per-WLAN client traffic stats accuracy enhancements
|
|
|
|
|
|
|
CSCux29207
|
Issue with SNMP GetBulk request - cLAPGroupsHyperlocationEnable
|
|
|
|
|
|
|
CSCux32328
|
Token Bucket leak with QoS Roles and with WebAuth on 8.0.120.2
|
|
|
|
|
|
|
CSCux37498
|
CoA with wlc 8.1.131.0 shows error message on ISE server
|
|
|
|
|
|
|
CSCux41577
|
WLC and AP out of SYNC for Client Exclusion List
|
|
|
|
|
|
|
CSCux45077
|
AP3500 crashed due to "LWAPP CLIENT" process.
|
|
|
|
|
|
|
CSCux47470
|
8.0.110.14 controller crash at openssl_cert_hash_algo_check_callback
|
|
|
|
|
|
|
CSCux51484
|
Memory leak observerd in EOGRE SNMP task
|
|
|
|
|
|
|
CSCux60012
|
With New Mobility - Mobility Members Don't survive reload
|
|
|
|
|
|
|
CSCux60873
|
Radius interface overwrite does not work when chosing "ap group" intf
|
|
|
|
|
|
|
CSCux65158
|
ATF : Globally configured mode not applied to newly joined APs
|
|
|
|
|
|
|
CSCux66190
|
No.of Interim Update Sent field is not flushing
|
|
|
|
|
|
|
CSCux69928
|
Wism2 Silent crash PMALLOC_DOUBLE_FREE on 8.0.122.18 MR3
|
|
|
|
|
|
|
CSCux74970
|
MAG w/PMIPv6 does not assign secondary DNS to clients via DHCP
|
|
|
|
|
|
|
CSCux75330
|
Mismatch AP count and unable to add more APs to WLC
|
|
|
|
|
|
|
CSCux78464
|
WLC crashes in Process Bonjour_Process_Task
|
|
|
|
|
|
|
CSCux81598
|
Memory Allocation problem with SAP1602
|
|
|
|
|
|
|
CSCux83260
|
BGL-Alpha: "lbs-ssc" &" sha256-lbs-ssc" missing in WLC web UI
|
|
|
|
|
|
|
CSCux83635
|
FATAL: Couldnt Send message out prints on 5500/7500 standby console
|
|
|
|
|
|
|
CSCux91996
|
Rogue containment not starting if no client info on best RSSI AP
|
|
|
|
|
|
|
CSCux92251
|
AIR-CAP2702 with WLC 8.2 doesnt allow HTTPS client access
|
|
|
|
|
|
|
CSCux93468
|
Anomalous Fan Speed/Temp reading for 8540
|
|
|
|
|
|
|
CSCux95607
|
ATF : User allowed to configure ATF on 1600 unsupported platform
|
|
|
|
|
|
|
CSCuy13829
|
AIR-CAP2602I crash on dot11_pmkid_timeout
|
|
|
|
|
|
|
CSCuy14547
|
HA Config Sync failed
|
|
|
|
|
|
|
CSCuy18768
|
Halo module doesn't work with RxSOP after image upgrade/dowgrade
|
|
|
|
|
|
|
CSCuy19485
|
Client detail table view miss alignment for a single client in bar graph
|
|
|
|
|
|
|
CSCuy21224
|
upport of 3G/4G module on 3600E/3700E APs
|
|
|
|
|
|
|
CSCuy23295
|
intf nasid given priority over wlan nasid in default Ap group
|
|
|
|
|
|
|
CSCuy33247
|
AP send disassociation frames twice and Optimized roaming go wrong
|
|
|
|
|
|
|
CSCuy37694
|
WLC crash running 8.0.120.0 at task apfRogueTask_1
|
|
|
|
|
|
|
CSCuy43365
|
5520 / 8540 8.2.100.0 Crash in Reaper Reset: Task "apfReceiveTask"
|
|
|
|
|
|
|
CSCuy45485
|
Containment to choose AP based on rogue client detected as well as RSSI
|
|
|
|
|
|
|
CSCuy45955
|
DFS scan causes beacon transmission to be stuck on AP
|
|
|
|
|
|
|
CSCuy47407
|
Client leak at anchor controller
|
|
|
|
|
|
|
CSCuy51343
|
Telnet/ssh config for AP is not retaining after upload/download config
|
|
|
|
|
|
|
CSCuy52607
|
Data Plane crash - cvmcs_StaToDS
|
|
|
|
|
|
|
CSCuy63742
|
Acct commands send inconsistently to TACACS server for rapid commands
|
|
|
|
|
|
|
CSCuy73622
|
Time sync failure for mmMsg_HandoffComplete on MC not printed on debugs
|
|
|
|
|
|
|
CSCuy92423
|
CWA broken in beta image 8.0.122.50
|
|
|
|
|
|
|
CSCuy94534
|
3700/2700 on DFS dont see 3700/2700 as neighbor when Rxsop High/Med/Low
|
|
|
|
|
|
|
CSCuy95327
|
802.1x frames are not marked with DSCP CS4
|
|
|
|
|
|
|
CSCuz01093
|
Traceback apf_site_override.c:2888 Invalid value 0 for WLAN
|
|
|
|
|
|
|
CSCuz02871
|
Webauth acl is not pushed from flexgroup when a new wlan is added to AP
|
|
|
|
|
|
|
CSCuz15763
|
Flex Data DTLS enabled AP gets stranded with WAN link flap
|
|
|
|
|
|
|
CSCuz22237
|
mobility express CORSICA: client not authenticated from 802.1x,wep)
|
|
|
|
|
|
|
CSCuz22985
|
BCAST Queue full causing Clients to stay Multicast-direct Pending status
|
|
|
|
|
|
|
CSCuz23758
|
Local Profiling Not Sorting Correctly, not corrected on 8.0.132
|
|
|
|
|
|
|
CSCuz24467
|
Mem corruption on GUI crash related to hreap avc group page
|
|
|
|
|
|
|
CSCuz38059
|
Anchor WLC does not free Client Sessions - client entries stale
|
|
|
|
|
|
|
CSCuz39100
|
ATF config not applied when no AP joined on controller
|
|
|
|
|
|
|
CSCuz46264
|
Flood of %SOCKET_TASK-7-DATA_PROCESSING_FAILED error messages
|
|
|
|
|
|
|
CSCuz47863
|
SHA256 self-signed cert for WLC web admin
|
|
|
|
|
|
|
CSCuz49616
|
WLAN-VLAN Mapping incorrect when AP moves across AP-Groups of diff WLANs
|
|
|
|
|
|
|
CSCuz52435
|
Evaluation of wlc for OpenSSL May 2016
|
|
|
|
|
|
|
CSCuz56009
|
Client reassoc not happening when central dhcp enabled
|
|
|
|
|
|
|
CSCuz56598
|
Enabling radio after disable/enable admin status,ifno channels available
|
|
|
|
|
|
|
CSCuz57198
|
SNMP AP3800:Clean air on xor radio is not functioning properly
|
|
|
|
|
|
|
CSCuz57392
|
AP3800 SNMP: Need errors for Channel Settings
|
|
|
|
|
|
|
CSCuz58908
|
AP3800 FRA configurations not retained in HA setup
|
|
|
|
|
|
|
CSCuz60033
|
WLC is dropping data packets in Hybrid VoWiFi setup
|
|
|
|
|
|
|
CSCuz63274
|
mDNS snooping drops IPv6 mDNS traffic
|
|
|
|
|
|
|
CSCuz67766
|
WLC crash due to software watchdog for apfMsConnTask_0
|
|
|
|
|
|
|
CSCuz68446
|
NOS: bsnAPIfTable has NULL entries
|
|
|
|
|
|
|
CSCuz69239
|
Flex local auth: 11n clients showing as 11ac
|
|
|
|
|
|
|
CSCuz70444
|
AP3800: XOR Microcell stuck on max power
|
|
|
|
|
|
|
CSCuz70999
|
AP3800: WLC crash while executing XOR radio commands
|
|
|
|
|
|
|
CSCuz71197
|
8500 wlc crash when starting 11v dms on sim clients
|
|
|
|
|
|
|
CSCuz72522
|
AP3800: FRA COF Metrics shows stale value for disabled Radios
|
|
|
|
|
|
|
CSCuz73422
|
1852 AP EAP-TLS client authentication fails
|
|
|
|
|
|
|
CSCuz73502
|
Spartan:2.4G data not shown for AP-Ch.Util,AP-Dist by SS,AP-Model Distr
|
|
|
|
|
|
|
CSCuz74209
|
AP3800: client network preference default is not default
|
|
|
|
|
|
|
CSCuz74637
|
WLC login banner does not show up on GUI. When using CLI it works fine.
|
|
|
|
|
|
|
CSCuz74989
|
AP3800: Issue setting channel for XOR radio in sniffer mode
|
|
|
|
|
|
|
CSCuz77060
|
SNMP:Radio Mode Trap generated when admin status changed for xor
|
|
|
|
|
|
|
CSCuz79051
|
WiSM2 8.1.131.0 crash in ewaFormServe_multicast_detail
|
|
|
|
|
|
|
CSCuz79869
|
8510 silent crash
|
|
|
|
|
|
|
CSCuz81176
|
AP3800: Beacons stuck seen in radio 0 & 1
|
|
|
|
|
|
|
CSCuz81415
|
1msec delay in processing IGMP packets causing Bcast queue to remain ful
|
|
|
|
|
|
|
CSCuz84096
|
RRM doesn't change channel for mesh APs in 8.1 and 8.2
|
|
|
|
|
|
|
CSCuz86679
|
5508 HA SSO crash on SNMPTask
|
|
|
|
|
|
|
CSCuz87680
|
WLC crashes with task:emweb on changing wlan config
|
|
|
|
|
|
|
CSCuz89491
|
BVI interface is down with latest recovery image
|
|
|
|
|
|
|
CSCuz89662
|
1852 Reject clients association due to "suppRates statusCode is 18"
|
|
|
|
|
|
|
CSCuz96571
|
Ap-list new mobility packets flooding between AirOS WLC
|
|
|
|
|
|
|
CSCuz97117
|
AP3800 CCO image "show inventory" displays incorrect SN & VID format
|
|
|
|
|
|
|
CSCva03344
|
Client capabilities shown as 160 MHZ even client is not 160MHZ
|
|
|
|
|
|
|
CSCva03888
|
3802 : DSCP marked as 0 in capwap header with CAC config
|
|
|
|
|
|
|
CSCva08910
|
Unable to view the client details by clicking on connection rate
|
|
|
|
|
|
|
CSCva09603
|
AP3800: 160 Mhz throws SNMP error
|
|
|
|
|
|
|
CSCva11172
|
No netflow records exported for anchored client in Auto Anchor Scenario
|
|
|
|
|
|
|
CSCva12198
|
SNMP get on device for table cld11nMcsTable returns only 24 indices
|
|
|
|
|
|
|
CSCva12984
|
DHCP_OPTION_43 functionality broken in AP3800 AP
|
|
|
|
|
|
|
CSCuz88260
|
Unable to handle kernel NULL ptr dereference at virtual addr 00000004
|
|
|
|
|
|
|
CSCva21709
|
1800 AP crashed - apsw_watchdog about to reboot with reason: capwapd
|
|
|
|
|
|
|
CSCva25338
|
2800/3800/1800 'show ap summary' displays wrong ip for static ip config
|
|
|
|
|
|
|
CSCuy67885
|
5520 or 8540 may have no Manufacturing Installed Certificates
|
|
|
|
|
|
|
CSCuz81177
|
2800/3800 Cmd timeout, RX Hang seen
|
|
|
|
|
|
|
CSCva07520
|
2800/3800 DP ERR>22>mv_dp_msg_check_rx:1747>FW Failure Status for opcode:7...
|
|
|
|
|
|
|
CSCux82102
|
AP 3600+11ac module crash on memory corruption for 8.2
|
|
|
|
|
|
|
CSCva14511
|
2800/3800/1800 DHCP_OPTION_43 messages not seen on AP console
|
|
|
|
|
|
|
CSCva13591
|
3802 AP fails to join the WLC after capwap restart
|
|
|
|
|
|
|
CSCva19392
|
2800/3800/1800 ERROR:receiveWlanMsg(): mgmt subtype:0xf len:1423 - dropped event
|
|
|
|
|
|
|
CSCva20303
|
5520 Mem Leak %APF-3-LIST_ERR: avc_api.c No entry available in table
|
|
|
|
|
|
|
CSCuy33972
|
WLC ssh host-key generate command not having an effect
|
|
|
|
|
|
|
CSCuz52725
|
2800/3800- Macbook is sometimes using 2SS rate on uplink
|
|
|
|
|
|
|
CSCva05657
|
3802 AP - cmd_to off channel stuck Tx FSM is not Idle & TCQ Verify zero
|
|
|
|
|
|
|
CSCva12610
|
2800/3800 -Clients are deauthenticating with EAPOL bcast interval expiry
|
|
|
|
|
|
|
CSCuz62398
|
1800 capwap local bcast discovery stops working on upgrade to 8.2.102.125
|
|
|
|
|
|
|
CSCva16181
|
2800/3800 Sniffer Mode set on XOR Band fails
|
|
|
|
|
|
|
CSCva21076
|
2800/3800/1800 Rx hang detection resulting in multiple radio resets & reboot
|
|
|
|
|
 Saturday, October 5, 2019 at 4:15PM
Saturday, October 5, 2019 at 4:15PM