WLC: Management via Wireless – Did you know ?
 Sunday, March 6, 2011 at 1:05AM
Sunday, March 6, 2011 at 1:05AM In recent weeks, I fielded a number of questions on the forums about “WLC Management via Wireless”. I thought, I would follow up with a quick blog post on the subject.
How it works:
On the Cisco WLC there is a security feature that allows you to ENABLE or DISABLE WLC management via wireless. But, there is a catch in exactly what to expect and how it works. Folks new to Cisco WLCs may not catch this right away or scratch their head when a WLC is disabled, but yet they can still access the WLC over the wireless medium.
When the management via wireless feature is disabled. Any wireless user (Admin or otherwise) will not be able to manage the Cisco WLC over wireless. HTTP,HTTPS,SSH and TELNET are ‘blocked’ from the wireless medium.
But, there is a catch:
When the management via wireless feature is DISABLE on the WLC, it only pertains to the WLC in which the wireless user is associated to. Wireless users can still manage (other) WLCs even though “Management via Wireless” is disabled.
Example:#1 ‘Management via Wireless Disabled’
The user in this example can not HTTP,HTTPS, SSH or TELNET into the controller management IP address in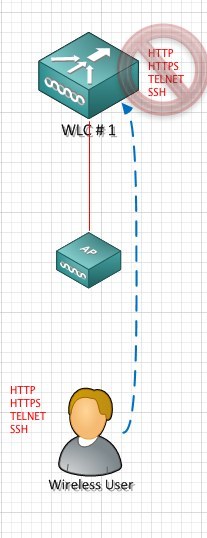 which they are associated to via the access point.
which they are associated to via the access point.
Example:#2 ‘Management via Wireless Disabled’
The user can access other WLCs (the ones he is not associated to), even though the management over wireless is disabled.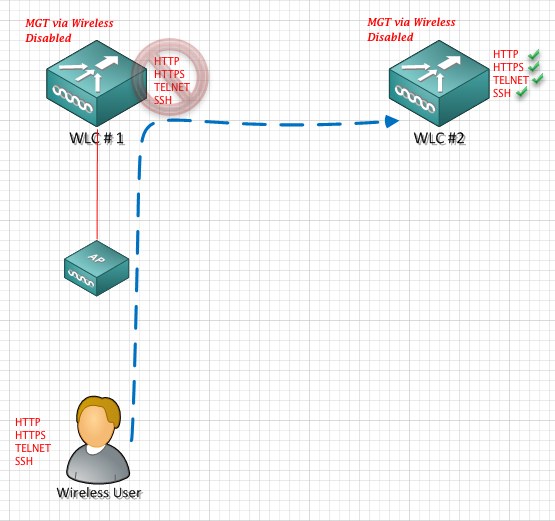
CLI Config:
In the CLI the >show network summary yields the status of the management via wireless
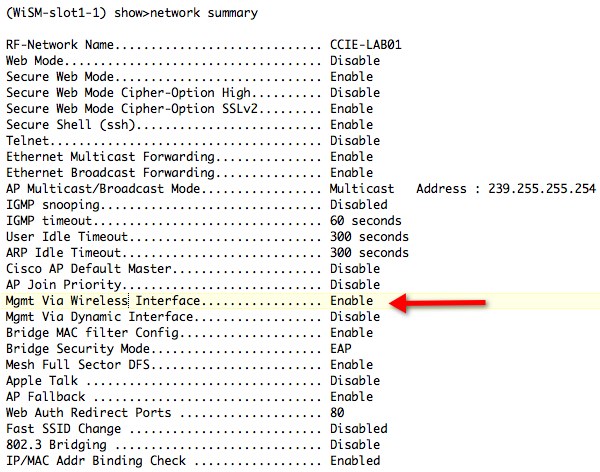
You can enable or disable management via wireless with the following CLI command:
> network mgmt-via-wireless
(WiSM-slot1-1) config>network mgmt-via-wireless ?
enable Enables this setting.
disable Disables this setting.
GUI Config:
In the GUI GO ->MANAGEMENT-> MGT Via WIRLESS -> (CHECK BOX)
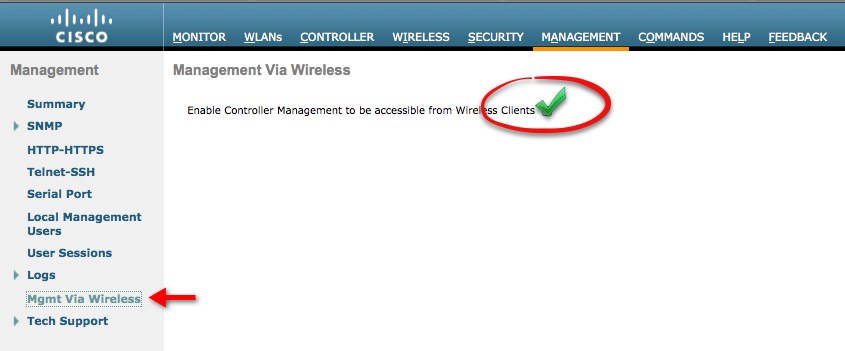















Reader Comments (4)
Here is some additional information on this particular widget that sometimes gets lost in the shuffle:
These are robbed wholesale from the FAQ at:
http://www.cisco.com/en/US/products/ps6366/products_qanda_item09186a008064a991.shtml
Q. With the Management via Wireless feature enabled on wireless LAN controllers (WLCs) in a mobility group, I can only access one WLC from that mobility group, but not all. Why?
A. This is an expected behavior. When enabled, the Management via Wireless feature allows a wireless client to reach or manage only the WLC to which its associated access point is registered. The client cannot manage other WLCs, even though these WLCs are in same mobility groups. This is implemented for security, and recently was tightened down to just the one WLC in order to limit exposure.
The Cisco WLAN Solution Management over Wireless feature allows Cisco WLAN Solution operators to monitor and configure local WLCs using a wireless client. This feature is supported for all management tasks, except uploads to and downloads from (transfers to and from) the WLC.
This is also a useful tidbit:
Usually, the management interface IP address is used for GUI and CLI access. Wireless clients can access the WLC only when the optionEnable Controller Management to be accessible from Wireless Clients is checked. In order to enable this option, click the Management menu of the WLC, and click Mgmt via Wireless on the left-hand side. WLC can also be accessed with one of its dynamic interface IP addresses. Use the config network mgmt-via-dynamic-interface command to enable this feature. Wired computers can have only CLI access with the dynamic interface of the WLC. Wireless clients have both CLI and GUI access with the dynamic interface.
Hey Sam,
Thanks for stopping by. I think Cisco has an error in their documentation. Because you can in fact reach other WLCs regardless of the mobility group with wireless management disabled. I think this is an issue myself. Thanks for the tidbit !
Nice article George. It's always confused me why this feature was left in by Cisco, as it gives a false sense of security in any topology except a single-controller deployment. In the event that a client wants to secure management traffic, a good approach is going to be to configuration of appropriate access control lists (on the layer 3 interfaces of the wired network is my personal preference) - do you agree?
Also, I think the same logic that is applied to 'management via wireless' also applies to the peer-to-peer blocking feature that can be applied to WLANs. Is that correct? (I guess that could be a whole other article)
Regards
Nigel.
I knew about this managment feature over wireless. I was suprised to see that my guest users can even try https to the managment IP over wireless. Even though
they are restricted on a ASA DMZ network with RFC1918 ACL denying all 10.x.xx. ,192.168.x.x, and 172.16.x.x network access. So there seem no other way
than the guest user can access the WLC directly over the capwapp tunnel. I put in a ACL on the WLAN (overide acl) with RFC1918 denies. I get hit on the deny
but still the user can ping the managment IP of the WLC and browse https to it. Does the allow wireless managment feature bypass all access list on the WLC ?
I am testing this on 4400 WLC with 7.0.220 code.