WLC:Generate Third Party Web Authentication Certificate for a WLC
 Sunday, January 16, 2011 at 8:34PM
Sunday, January 16, 2011 at 8:34PM It’s that time of year and our Cisco WLC Web Authentication Certificate is close to expiration. Certificates are not my strong point and its not often I have to deal with them outside of ACS and the controllers. So I wanted to document these steps for my benefit for next go around.
This is a step by step “how to” creating a CSR (Certificate Signing Request) with OPENSSL, processing a third-party certificate that is CHAINED and download it to the Cisco WLC.
Dependency Homework
Its always important to check your dependencies and NEVER assume.
1) WLC versions earlier than 5.1.151.0, web authentication certificates can be only device certificates and DO NOT support chained certificates, ONLY ROOT SIGNED certificates
2) WLC versions 5.1.151.0 and later support chained certificates (up to a level of 2)
3) ** Certificate Levels **
Level 0 – Use of only a server certificate on WLC
Level 1 – Use of server certificate on WLC and a CA root certificate
Level 2 – Use of server certificate on WLC, one single CA intermediate certificate, and a CA root certificate.
Level 3 - Use of server certificate on WLC, two CA intermediate certificate, and a CA root certificate.
4) Entrust does not support root signed certificates (unchained) as of 12/31/2010. Since my anchors are on 4.2.x, looks like I will be upgrading my controller code.
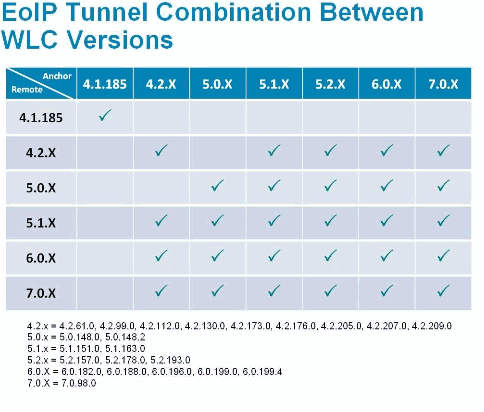
5) When anchoring, the remote and anchor controllers connect using EoIP tunnels. Below is a quick look at supported code levels . Although, Cisco will tell you its best practice to have your Anchors and Remote WLCs on the same version of code.
Why a signed certificate on the Cisco Anchor WLC?
The Anchor WLC is configured with HTTPS. When a guest user connects to the wireless guest network they will be presented with a WLC self signed certificate or an expired certificate. As such, this will cause the “please accept” this certificate screen.
By installed a signed CA certificate, you negate this screen and users move directly to the accept screen. Its really a inconvenience to the end user.
OPENSSL
If this is your first time using OPENSSL, it could be a little intimidating, but it isn’t really as bad as you think. Everything is scripted.
Before starting, you will need to download and unzip OPENSSL. You will notice a number of versions. I used windows version ,0.9.8.a to create my CSR. I unzipped OPENSSL in a folder off my C: drive
C:\openssl>
Generate a CSR
A CSR stands for certificate signing request. This is the first step in the certificate process.
After you have OPENSSL installed you want to launch openssl.exe. You then enter the following script.
1) C:\openssl\bin>openssl.exe
OpenSSL> req –new –newkey rsa:2048 –nodes –keyout mykey.pem –out myreq.pem
Note: The WLC supports a maximum key size of 2048
2) You will be presented with a number of questions. Your company name, state, country, common name etc. Its important to enter this information correctly. This data gets checked against the CA information on file. It is also important the CN (common name) matches the DNS A record for your virtual IP.
You will also be prompted to enter an optional password. This is important, as it adds an extra layer of security and prevents someone compiling the certificate without the password.
OpenSSL>req −new −newkey rsa:2048 −nodes −keyout mykey.pem −out myreq.pem
Loading 'screen' into random state − done Generating a 2048 bit RSA private key ................................................................++++++ ...................................................++++++
writing new private key to 'mykey.pem'
−−−−−
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank
For some fields there will be a default value, If you enter '.', the field will be left blank.
−−−−−
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some−State]:TX
Locality Name (eg, city) []:Houston
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Mycompany
Organizational Unit Name (eg, section) []:IT
Common Name (eg, YOUR name) []:guest.yourhospital.org
Email Address []:it@mycompany.com
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []:TESTEST
An optional company name []:
OpenSSL>
3) Once you are complete. You will find 2 files in the bin folder.
- mykey.pem
- myreq.pem
The mykey.pem is your portion of the CSR which will be used later. Keep this in a safe place.
The myreq.pem is your CSR ,which is sent to your CA. If you change the file type from .pem to .txt you will see something similar to this:
4) The CA will reply with a digitally signed certificate chain. You will receive three certificates.
- Root Certificate
- Intermediate Certificate
- Device Certificate
5) The next step, you will want to take the 3 certificates and change the extension to .txt.
Entrust.cer
L1Cchainroot.cer
L1Croot.cer
Once the extensions are converted to .txt. Open notepad and cut and paste the certificates in this order:
−−−−−−BEGIN CERTIFICATE−−−−−−
*Device cert*
−−−−−−END CERTIFICATE−−−−−−
−−−−−−BEGIN CERTIFICATE−−−−−−
*Intermediate CA cert *
−−−−−−END CERTIFICATE−−−−−−−−
−−−−−−BEGIN CERTIFICATE−−−−−−
*Root CA cert *
−−−−−−END CERTIFICATE−−−−−−
 **NOTE THESE ARE NOT REAL CERTIFICATES**
**NOTE THESE ARE NOT REAL CERTIFICATES**
It is important you put the certs in the correct order -- device, intermediate, root.
- Device Certificate
- Intermediate Certificate
- Root Certificate
Specific to Entrust … your cert order would be the following:
- Device Certificate ------------------ L1Croot
- Intermediate Certificate-----------L1Cchainroot
- Root Certificate----------------------Entrust
**NOTE IF YOU OPEN THE ROOT CERTIFICATE THIS WILL CONTAIN YOUR CN (COMMON NAME) **
6) Save the file as All-certs.pem
7) In this step you will combine your mykey.pem and the All-certs.pem. Open up OPENSLL again. Enter the following:
C:\openssl\bin>openssl.exe
OpenSSL> pkcs12 -export -in All-certs.pem -inkey mykey.pem -out All-certs.p12 -clcerts -passin pass:TESTTEST -passout pass:TESTTEST
Loading 'screen' into random state - done
OpenSSL> pkcs12 -in All-certs.p12 -out final-cert.pem -passin pass:TESTTEST -passout pass:TESTTEST
MAC verified OK
OpenSSL>
**NOTE YOU ENTER THE PASSWORD YOU CREATED DURING THE CSR CREATION **
8) When you are done you will have 1 file, called final-cert.pem. This is the certificate you will download to your Anchor WLC.
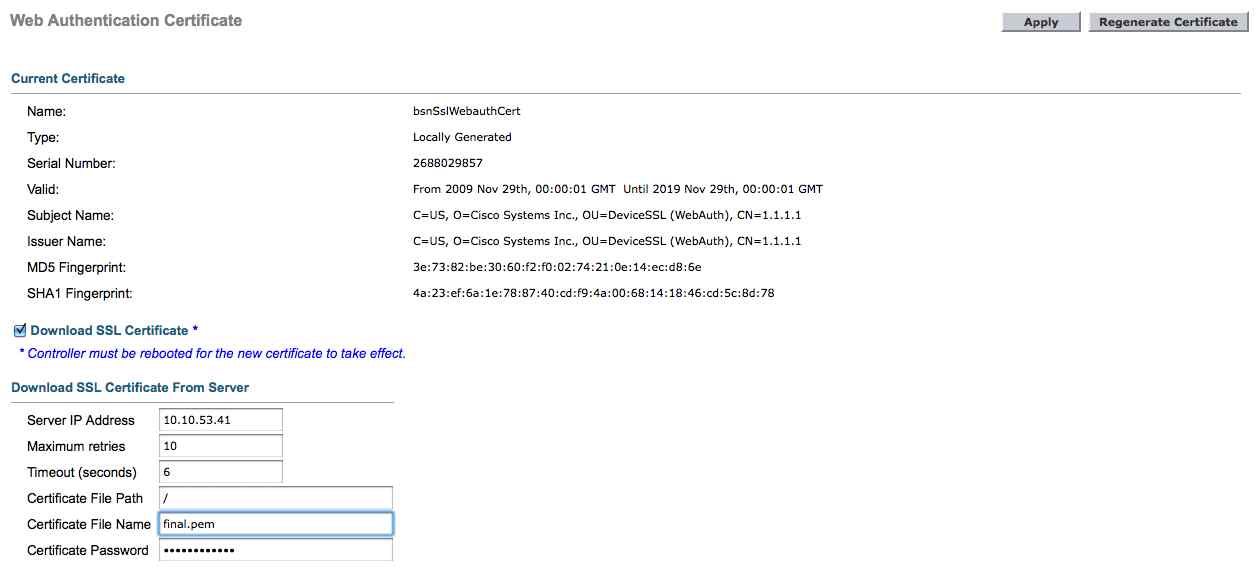
9) Enter your WLC Security ->Web Auth -> Certificate
Check, check box “Download SSL Certifciate” and enter your TFTP information and your certificate password.
 George
George
Some addiitonal Cisco info to help:
https://supportforums.cisco.com/docs/DOC-27773#comment-14282















Reader Comments (12)
Thank you for posting this process. I was unsure of OPENSSL, but it looks pretty easy.
Thanks a lot for discussing this matter. I concur with your conclusions.The point that the data stated are all first hand on actual experiences even help more.
on the controller you selected file name as final.pem. It should be final-cert.pem as this is the file name that we put in last command.
How can we check the common name in the root cert or how it gets highlighted.
Any idea, if wildcard is also supported on cisco controllers?
I got the cert loaded but here is my issue:
- Since how do I get the guest.mydomain.com to resolve to 1.1.1.1?
- The way it is setup clients do not have access to the internal DNS only external DNS i.e; OpenDNS servers
- I tried changing the Virtual interfaces IP address but when I do that none of the clients can grab an IP address since I am using the WLC as the DHCP server with DHCP proxy enabled Virtual interfaces IP needs to stay as 1.1.1.1.
Any help would be appreciated thank you.
Thanks a bunch! Really helpful and easy to follow!
I didn't get 3 files back from my CA only a x509 .cer or a .p7b file. If I open the .cer, it shows the full certificate path, yet on my WLC it does not?
Do you know, or can you help me understand-what is the relationship of the cert installed on the WLC compared to a radius server? For example, we are using IAS on W2K3 server. I installed a 3rd party cert on the wlc as well as on IAS. When connecting to the wlan from a Windows 7 or Mac client, I get a certificate error (can't connect at all from XP). I changed the IAS cert to a local CA and left the WLC as a 3rd party cert, and the error message on the client remains, but now lists the IAS server cert as untrusted. I think I have spent too much time looking and over-engineering this, and have confused myself. TIA.
Yup no worries. The cert loaded on the WLC is your web browser certificate. The cert loaded on the radius server is used for 802.1X authenticatin for example with PEAP. if you add the local cert to your cert store you will not get prompted to trust the cert.
Hi George, wondered if you've done a guest solution with foregin, anchor and NAC Guest Server hosting the web-login page? I think that I need certs on all devices but I'm not 100% sure.
This is an excellent description, which carried me through the whole run from creating a CSR to installing the final certificate. Appreciated.
Ole, thanks for stopping by .....
I just read through the entire article of yours and it was quite good. This is a great article thanks for sharing this information. I will visit your blog regularly for some latest post.
中古車査定